Operate On A Secure Network
Public free Wi-Fi hotspots are usually a gateway for malware attacks. Try to avoid these if possible, as these are very easy to spoof.
If you have to use these, then be very wary of any suspicious activity on your browsing and try to keep the connected session at the minimum.
Disconnect at the first sign of suspicious activity to avoid any further damage and run a full system scan to detect any potential threats that may have gone in unnoticed.
For How To Get Malware: Falling For Phishing Attacks
Phishing is a cyber attack method that uses social engineering tactics to extract personal information from victims. Cybercriminals often carry out phishing attacks in such a way that the victim believes the cybercriminal is a legitimate person. This is because bad guys present themselves as trusted authorities government or law enforcement representatives or company executives to get you to trust them and comply. They then either use the information you provide to carry out other crimes or sell it to other cybercriminals.
FBI IC3 reported 241,342 complaints of phishing in 2020 as opposed to 114,702 in 2019 . According to Proofpoint, 57% of global survey respondents said their organizations deal with at least one successful phishing attack in 2020.
There are many ways that cybercriminals can use phishing to their advantage. Lets explore a few
Email Phishing Attacks
Emails are one of the most common techniques to carry out phishing attacks. Verizons 2020 Data Breach Investigations Report data indicates that around 46% of organizations received all the malware was delivered through email.
There are many types of phishing scams that bad guys will use to target potential victims, such as pretending to be a vendor or an executive within your organization. Theyll use a variety of tactics to make their emails appear legitimate to get you to download and install malware, including:
SMS Phishing Attacks
Voice Phishing Attacks
Spear Phishing Attacks
For How To Get Malware: Visiting Malicious Websites
Alright, weve reached the last item on our list of how to get malware infections. This one focuses on how bad guys use malicious URLs to spread malware.
Phishing emails might be used to send links to fake websites that resemble legitimate ones. When the user opens this fake website, they might be asked to log in to access their account. This is actually a phishing scam that allows bad guys to steal your user credentials. However, in some cases, the website links are even more sinister because they take you to sites containing malware. Those sites will instead infect your device.
Cybercriminals sometimes use typosquatting as well to make their fake websites URLs appear more legitimate. This helps users reach their sites by simply misspelling or mistyping the domain name. Here are a few quick examples of how this works:
- Swap letters or numbers with other similar-looking characters. For example, the letter I can be replaced with l, .
- Replace single characters with combinations. The letter m can be replaced with rn Amazon.com can be Arnazon.com or
- Add or remove characters to/from domains. An extra letter can be added or removed to create similar-looking domain names. For example, apple.com can become appple.com, and blogger.com can become bloger.com.
Also Check: How To Get Over A Kidney Infection
Ways To Avoid Malware Infection In Software Patches
The objective of a software patch is to eliminate a vulnerability or fix a software flaw that is identified after the software is released, add new functionality or improve performance. Timely installation of newly released patches is an important maintenance step. It keeps your systems current and stable, optimizes performance, and mitigates the threat of new malware infection.
Timely application of software patches is absolutely critical, yet recent surveys indicate that:
- 60% of respondents reported that data breaches involved vulnerabilities for which a patch was available but not applied.
- 68% of respondents believe that data breaches occur because of poorly executed patch management.
Keep Your System Update

Remember the Equifax breach? Its possible this massive attack could have been prevented if the company had just made sure its security software was . Whenever you get an alert about an update to anything including plugins dont ignore it. It may seem inconvenient, but maximum protection is always worthwhile, and these updates can usually be run during off-hours.
Recommended Reading: Fastest Way To Cure A Bladder Infection
Lockdown Your Smart Devices
Internet connectivity is finding its way into more and more of our home devices. While smart devices might be ushering in a new era of convenience and efficiency, each Internet-connected device also provides a possible point of entry for malware attacks.
Below are a few tips to keep your smart devices secure:
- Apply network segmentation to isolate your smart devices on their own network and prevent an attack from spreading to your more important devices.
- Change the default passwords on all of your Internet-connected devices.
- Apply software and firmware updates when available.
- Secure your router using the best practices described earlier.
Avoid Running Programs That Launch Suspiciously
Anti-viruses, however, are not a sure-fire way of getting protected from malware since they are more reactive to threats.
So if youre unfortunate enough to be hit by a zero-day malware, then youre out of luck when it comes to detecting it.
Or maybe not since Application Whitelisting is the best 2nd layer of defense that you can add to ensure that even zero-day malware cant get through behind your back.
Malware usually tries to run without you knowing by downloading themselves via a drive-by download while trying its best to remain undetected by antivirus software.
As long as these cant run, however, they stay harmless even if they download themselves on to your PC.
Luckily enough SecureAPlus is the ultimate companion for most anti-malware solutions today.
It offers reliable malware protection combined with that of every other anti-malware, anti-virus, and anti-spyware you have in your computer, making it easier to find threats, which others missed.
The best part is that it is free for a year, so everyone can download it to keep his or her computers safe from all possible harm.
There is nothing better than software that offers free malware removal and prevention to provide reliable protection for your computer.
With some common sense, SecureAPlus is just the ideal program to keep your PC malware-free.
You May Like: Yeast Infection On Your Period
Why Cisco For Malware Protection
Cisco has developed comprehensive security software solutions to help manage every aspect of network security across your organization. Whether you need to provide enterprise security or simplify information security for a small business, the Cisco Security portfolio provides advanced Next-Generation Firewall protection and data and application security.
Simplified network security software allows IT staff to quickly deploy a rigid security policy so your IT department can instantly leverage the power of SaaS security solutions, including endpoint security solutions. Upgrade your security profile to the highest level and harness the true power of your network.
Cisco Security solutions–including Duo two-factor authentication, Umbrella, and AMP for Endpoints–provide prevention, detection, and response for an integrated, proactive cybersecurity approach.
University Requirements And Policies
As per the University IT security policy and standards, all University-owned devices connected to the University network must run current, up-to-date anti-malware protection software. Anti-malware protection software is recommended for other devices, including personal devices that connect to the University network.
For more information on relevant University IT security policies and standards, refer to Cyber security policies and guidelines.
Don’t Miss: Can I Infect Someone While On Prep
Backup Software Protection Or Threat
If you do not want to protect your data manually, you can use what is known as backup software. But here you also need to exercise caution. That’s because some “security tools” can also turn out to be Trojans. Creating backup copies is a primary task of backup software, which means it has access to all files and has numerous privileges.
Software usually has a direct connection to the provider, so it is easy for cybercriminals to incorporate additional functions and commands. These can be harmful and may not be recognized by the user. In order to avoid such a situation, you should be very careful when searching for suitable backup software. Some security solutions, such as Kaspersky Total Security Tool, already offer plug-ins that can create backups. By using this kind of plug-in, you can avoid having to search for third-party providers.
How To Avoid Malware Infections
February 23, 2015// by ccadmin
Malware is a term used to describe a broad category of damaging software that includes viruses, worms, trojan horses, rootkits, spyware, and adware. The effects of malware range from brief annoyance to computer crashes and identity theft. Malware is easier to avoid than it is to remove. Avoiding malware involves a two-part strategy. Follow these guidelines for staying safe.
Also Check: 8 Hour Infection Control Course For Dental Assistants
How Can I Get Infected
Users who visit malicious or compromised websites may have downloaded the malware, unwittingly. Malware can also arrive as a payload that another malware have either dropped or downloaded. Some are delivered as attachments to spammed email.
Once ran in the device, a malware can either do things such as exploitation, remote control, information theft, deception, corruption and more.
Always Check If You Are Visiting A Secure Site

The other way you can avoid malware infection on your computer is avoiding content from non-secure sites.
To know that the website your visiting is secure, look at the address bar and see if theres a lock before the URL. If its not there, know youre putting yourself at risk.
Some browsers such as Mozilla and Chrome warn users of mixed content. When a secure HTTPS webpage pulls content from non-secure HTTP sources, Chrome, Mozilla, and other browsers will warn users that the site is not safe.
In addition to the Lock icons, Mozilla has up to three other indicators
A green lock with a grey warning over it
This lock is used when the site has mixed content that is the site could be safe but containing uploads from external sources.
A grey lock with a red slash through it
This lock is shown when the certificate has expired but the user can still be able to access the content on the site.
A grey lock with a yellow warning triangle over it
This sign is displayed on the browser when sites are using deprecated cryptography. This means that the site content is not approved or not secure for access.
It also means that the resources are not secure and can be viewed by others while in transit. This makes it vulnerable to malware.
With the above, I hope youll be able to protect your computer and avoid malware infection.
Related:
You May Like: Does Cephalexin Treat Ear Infections
Examples Of Malware Attacks: Ransomware
As we mentioned above, the use of ransomware in malware attacks has snowballed in recent years. Statista reports that there were 304M ransomware attacks in 2020 up from 184M in 2017. Here are a few ransomware attacks that have grabbed headlines:
- A Conti ransomware attack blacked out the Health Service Executives IT systems in May 2021.
- The ransomware group Babuk hit Houston Rockets in April of 2021.
Ransomware attacks have become adept at disabling the security software running inside target endpoints. This was particularly notable in the Hades cases, where the malicious actors knocked out both the antivirus and the endpoint detection & response software that was in place. As we will cover later in this article, this is an important reason why it is essential to include edge protections in your security stack that are unable to be corrupted by infected endpoints.
How To Tell If You’ve Been Infected:
Before you can recover from an infection, you need to find it. Below are some telltale signs that you have been infected by malware.
- You are being asked for personal information or are urged to do something urgently
- Pop-up windows, especially ones claming to be anti-virus software
- Computer gets caught in a “reboot loop”
- Computer starts playing funny sounds or starts talking to you
Recommended Reading: Diflucan 1 Dose Yeast Infection
Easy Ways To Prevent Malware Infection
Posted: by Wendy Zamora
We told you how to tell if you’re infected with malware. We told you how to clean up the infection if you were affected. But how about we prevent malware infection from happening in the first place!
Yes, it’s possible to clean up an infected computer and fully remove malware from your system. But the damage from some forms of malware, like ransomware, cannot be undone. If they’ve encrypted your files and you haven’t backed them up, the jig is up. So your best defense is to beat the bad guys at their own game.
While no single method is ever 100 percent fool-proof, there are some tried and true cybersecurity techniques for keeping malware infections at bay that, if put into practice, will shield you from most of the garbage of the Internet.
Without further ado:
The Umbrella Term Malware Is One Of The Greatest Cybersecurity Threats Enterprises Face Learn About 10 Common Types Of Malware And How To Prevent Them
- Isabella Harford,Assistant Site Editor
Malware is one of the greatest security threats enterprises face. Malware attacks increased 358% in 2020 over 2019, and ransomware attacks increased 435% year over year, according to Deep Instinct. 2021 is setting up to be more of the same. The first half of the year saw 93% more ransomware attacks than the same period in 2020, according to Check Point’s midyear security report.
Security departments must actively monitor networks to catch and contain malware before it can cause extensive damage. With malware, however, prevention is key. But, to prevent an attack, it is critical to first understand what malware is, along with the 10 most common types of malware.
Read Also: Hot Or Cold Compress For Tooth Infection
Use Encryption To Secure Data In Transit
Cybercriminals use every possible opportunity to hijack your data, including the time when it is in transit. The conversation between the website and server, the email correspondence with outsiders, the internal correspondence of the organization can be intercepted and used by the bad guys for their malicious purposes. The enterprise must keep the data-in-transit secure from their prying eyes. Some of the ways to achieve this goal are as follows:
Use SSL/TLS Certification For Your Website
An SSL/TLS certificate is a digital certificate thats a core component of public key infrastructure . Its what organizations use to authenticate their servers and establish secure, encrypted connections between their websites and users web clients. This is what makes the HTTPS appear in your browsers address bar!
Most browsers brand websites as being not secure if they dont have TLS certificates installed. The visitors trust in your website dwindles when they see this ugly warning in their browsers address bar. Needless to say, HTTPS plays a pivotal role in a companys online business.
Use Email Security Tools like S/MIME Certificates to Protect Sensitive Messages
It works by having you encrypt the email using the recipients public key, which they can decrypt upon receipt using their corresponding private key. This process ensures data integrity and secures your message before it leaves your mailbox.
How Can I Get Rid Of Malware
How to remove viruses and other malware from your Android device
What are the warning signs of malware?
7 signs you have malware and how to get rid of it
- Contextual ads are starting to appear everywhere.
- Your browser continues to be redirected.
- An unknown app sends scary warnings.
- Mysterious posts appear on your social networks.
- You get ransom demands.
- Your system tools are disabled.
- Everything seems perfectly normal.
Read Also: Virtual Doctor Visit Ear Infection
Use Network And Endpoint Security Tools
First on our list of how to prevent malware attacks: use the right tools. Your IT experts should look into every possible route through which a criminal can use malware attacks against your organizations devices and network. Using a combination of endpoint and network security protection tools is the answer to preventing many malware-related security woes.
Install Antivirus or Anti-Malware Software
Antivirus and anti-malware tools are useful for identifying and protecting your endpoint devices or larger network against many traditional and new malware-related threats. And its easy to see why such tools are necessary considering that Kaspersky detected an average of 360,000 new malicious files every day in 2020.
Different antivirus and anti-malware tools offer varying levels of protection:
Use A Firewall
A firewall is another layer of protection that gives you more robust security of your devices and network. A firewall acts as a barrier between the internet and your IT infrastructure, blocking many types of malware attacks and other malicious activities . They come in hardware and software varieties, although many organizations use both. So, if youre wondering how to prevent malware attacks, this is a good way to do it.
Keep Your Online Browsing On Trusted Sources
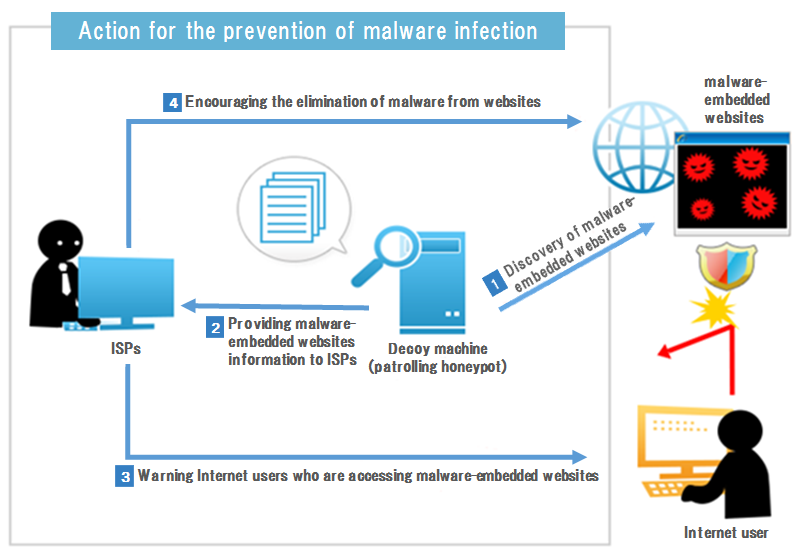
People used to browse for information on the web by searching for topics on search engines like Google & Yahoo, and these usually do an excellent job of filtering out malicious sites from the top search results.
Nowadays, social media is so ingrained into our daily lives that we usually consume content via suggestions from the social media feed. While these may be an excellent way to find new sources of information, its still best to keep to reputable sources rather than carelessly clicking on lesser known ones.
Those with controversial or exaggerated headlines that try to get your attention, otherwise known as click-bait articles, are very common and are now being exploited by malware creators.
These can be created by malware engineers to facilitate a drive-by-download without the user ever knowing theyve been infected.
Smaller sites are prone to be hacked due to poor web security practices and could do the same to unsuspecting visitors.
Be sure to think before you click on any of these.
Also Check: Fluconazole 150 Mg Tablet For Yeast Infection