Check Activity Monitor For Mac Malware
If you suspect your Mac has been infected with a virus, one of the best places to look is Activity Monitor. Here, youll be able to see background processes and apps that are running including malware.
How to check Activity Monitor for Mac viruses:
1. Open Activity Monitor from Applications > Utilities
2. Go to the CPU tab, if youre not already in it
3. Click the % CPU column to sort high to low, and look for high CPU use
4. If you see a process that looks suspicious, do a Google search on it. You should find information that confirms whether or not its malware
How Can I Protect My Iphone From Pegasus
This spyware uses many attack methods known and unknown, but there are some steps you can take to reduce your chances of being compromised:
- It should go without saying that you need to secure your phone with a PIN or preferably a strong password.
- Update the operating system regularly.
- Uninstall apps you dont use to minimize the attack surface. Facetime, Apple Music, Mail, and iMessage are known to be vulnerable to the Pegasus infection, but you probably use at least a couple of them.
- Reboot your phone at least once a day as this can clear the spyware from RAM and make life more difficult for it to work properly.
- Dont click on links in any messages from unknown numbers, even if you are expecting a parcel delivery.
Remove Malware From Browsing Extensions
Now that you know about malware removal Mac computers have another place to look: browsers.
Browser extensions run when a browser is being used, but for most of us, thats just about all day, every day. Browsers are basic tools to access the internet but can be very powerful, too.
If you use Chrome, extensions can be managed by selecting Window in the Mac menu bar when Chrome is open, then Extensions. This takes you to a dedicated page in Chrome where you can disable or remove extensions.
In Firefox, you can select Add-ons from the settings menu in the top right of the browser window, then Extensions from the list on the left side of the browser window. This page allows you to disable or remove extensions.
In Safari, extensions are a bit tougher to get to. You have to select Safari from the menu bar, then Preferences. In that window is a tab named Extensions where you can disable or uninstall your extensions.
Not all extensions are bad and not all trusted extensions are good! A great way to know if an extension is doing more than it should is to use iStat Menus, an app that monitors your Mac performance, including browsers and extensions.
Computer performance is an indicator of malware, and iStat Menus gives you a real-time look at what apps or extensions are using resources on your Mac, then offering to delete them.
Also Check: Best Antibiotic For Severe Sinus Infection
Removing Adware And Pop
It can be difficult to get rid adware, so we’ve created this article to assist you in removing these unwanted pop-ups and advertisements on your Mac. It’s important to follow all of the instructions outlined below. If you have any questions or concerns about completing these steps as listed, we recommend Contacting Intego Support for further assistance. To completely remove adware and pop-ups from your Mac, follow these steps in order:
Are There Serious Alternatives To Ios And Android Phones
At the time of writing the mobile OS ecosystem suffers a serious lack of diversity and even hardened Android forks such as Graphene OS or Calyx may offer no protection. Security-through-obscurity might be applicable in this case and a device running Sailfish OS from Jolla or perhaps a Librem 5 running Pure OS are the main alternatives.
Related:Most Secure Phones for Privacy
Read Also: Best Medication For Kidney Infection
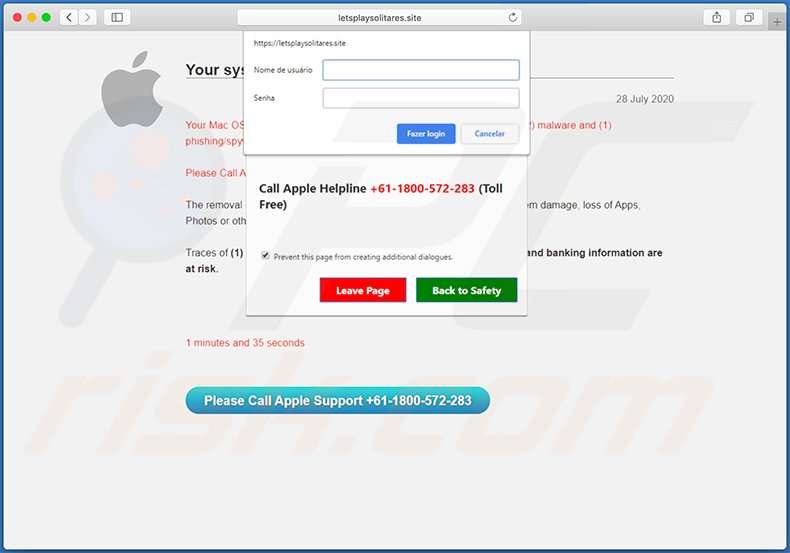
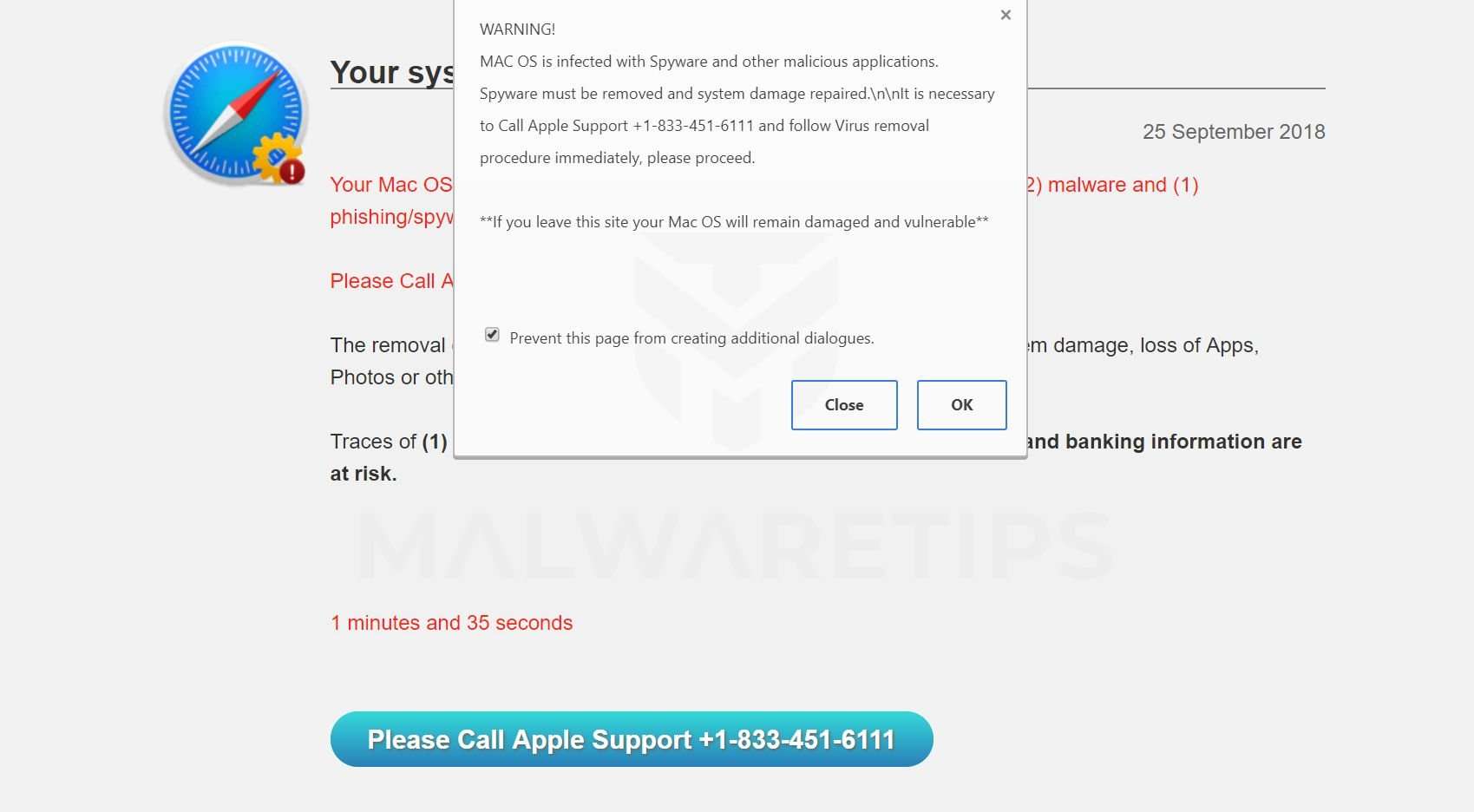
Is Mac Os Is Infected With Spyware A Scam
Bottom line up front, yes, MAC OS is infected with Spyware is a tech support scam and you should avoid it, moreover, refrain from calling. For someone who has never come across this type of virtual fraud, at first, the pop-up can look very believable, especially when back in the day the real technical support was provided remotely pretty often. However, the true services would never lock your browser, lie about your system having a virus, in the same page giving their number for you to call. But that is not the only questionable feature of this scam.
Our researchers found out that this exact Official Apple Support scam has been active at least for around a year. The reason why it did not get caught yet, was because it kept changing domains and provided numbers. So even if the URL and contact info would differ, the message would stay the same:
WARNING!
MAC OS is infected with Spyware and other malicious applications. Spyware must be removed and system damage repaired. It is necessary to Call Apple Support +1-888-514-0187 and follow Virus removal procedures immediately, please proceed.
** If you leave this site your Mac OS will remain damaged and vulnerable**
- 888-514-0187
- 877-314-0111
- 855-246-5422
What To Do If You Fell For A Pop
This depends on the type of scam that you fell for. Most commonly, pop-up scams try to trick users into sending money, giving away personal information, or giving access to one’s device.
- If you sent money to scammers: You should contact your financial institution and explain that you were scammed. If informed promptly, there’s a chance to get your money back.
- If you gave away your personal information: You should change your passwords and enable two-factor authentication in all online services that you use. Visit Federal Trade Commission to report identity theft and get personalized recovery steps.
- If you let scammers connect to your device: You should scan your computer with reputable anti-malware – cyber criminals could have planted trojans, keyloggers, and other malware, don’t use your computer until removing possible threats.
- Help other Internet users: report Internet scams to Federal Trade Commission.
Show Discussion
About the author:
Tomas Meskauskas – expert security researcher, professional malware analyst.
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on and to stay informed about the latest online security threats. Contact Tomas Meskauskas.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Read Also: Bladder Infection Not Going Away
How To Get Rid Of Mac Os Is Infected With Spyware Fake Alerts Without Any Software
The steps will help you remove MAC OS is infected with Spyware popup scam. These removal steps work for the Google Chrome, Safari and Mozilla Firefox, as well as every version of MAC operating system.
Remove adware through the Finder
The process of adware removal is generally the same across all versions of Mac OS. To start with, its necessary to check the list of installed apps on your MAC system and delete all unused, unknown and dubious applications.
Open Finder and click Applications.
Carefully browse through the list of installed applications and get rid of all suspicious and unknown apps.
After youve found anything suspicious that may be the ad supported software that shows misleading MAC OS is infected with Spyware popup scam on your Apple Mac or other PUP , then right click this program and select Move to Trash. Once complete, Empty Trash.
Remove MAC OS is infected with Spyware popup warnings from Safari
If you find that Safari web browser settings having been changed by adware that causes web-browsers to open misleading MAC OS is infected with Spyware fake alerts, then you may revert back your settings, via the reset web browser procedure.
It will open the Safari Preferences window. Next, click the Extensions tab. Look for unknown and suspicious plugins on left panel, choose it, then press the Uninstall button. Most important to remove all unknown add-ons from Safari.
Find the Homepage and type into textfield https://www.google.com.
How To Detect Spyware
Even if you can’t find the spyware program, you may be able to detect signs of it. For instance, if a computer starts to run more and more slowly, that could be a sign that it has been compromised. Look out for the following clues:
- Increasing sluggishness and slow response.
- Unexpected advertising messages or pop-ups .
- New toolbars, search engines and internet home pages that you don’t remember installing.
- Batteries becoming depleted more quickly than usual.
- Difficulty logging into secure sites.
- Inexplicable increases in your data usage or bandwidth use. These can be a sign that the spyware is searching your information and uploading data to a third party.
- Anti-virus and other safety software not working.
- How can you detect spyware on an Android phone? If you look in Settings, you’ll see a setting which allows apps to be downloaded and installed that aren’t in the Google Play Store. If this has been enabled, it’s a sign that potential spyware may have been installed by accident.
- How can you detect spyware on an iPhone? Look for an app called Cydia, which enables users to install software on a jailbroken phone. If it’s there and you didn’t install it, remove it immediately.
Read Also: Guidelines For Environmental Infection Control In Health Care Facilities
Wondering How Many Viruses Exist For The Mac Here Is A List Recent Mac Malware Attacks Viruses For Apple Computers And Security Threats That Mac Users Have Suffered
ByKaren Haslam, Editor| 22 Jul 21
Despite Apple’s best efforts, Mac malware does exist, we describe some cases below. However, before you panic, Mac malware and viruses are very rarely found “in the wild”.
From time to time you will hear of big profile trojans, malware, and ransomware that is targetting the Windows world, very rarely is this a threat to Macs. For example, the WannaCry/WannaCrypt ransomware that bought the NHS to its knees in May 2017 was only targetting Windows machines and therefore no threat to Macs.
Luckily Apple has various measures in place to guard against such threats. For example, macOS shouldn’t allow the installation of third-party software unless it’s from the App Store or identified developers, as per the Security & Privacy settings, that you can access in System Preferences > Security & Privacy > General. If you were to install something from an unknown developer Apple would warn you to check it’s authenticity.
In addition Apple has its own built-in anti-malware tool. Apple has all the malware definitions in its XProtect file which sits on your Mac, and everytime you download a new application it checks that none of those definitions are present. This is part of Apple’s Gatekeeper software that blocks apps created by malware developers and verifies that apps haven’t been tampered with. For more information read: how Apple protects you from malware.
- OSX.Generic.Suspicious 80.65%
- OSX.Adwind 0.1%
- OSX.KeRanger 0.1%
Remove From Mozilla Firefox
Remove it now ReimageUninstallTermsPrivacyIntegoUninstallTermsPrivacy
Remove dangerous extensions:
Reset the homepage:
Clear cookies and site data:
Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
To get rid of all unknown extensions and other objects from Google Chrome, try completing the below-provided guidelines.
Delete malicious extensions from Google Chrome:
Clear cache and web data from Chrome:
Recommended Reading: Antibiotics For Uti Bladder Infection
Disconnect Your Mac From The Internet
If it looks like your Mac has been affected by some virus, make sure you disconnect from the Internet immediately. This wont alleviate the harm thats already been done, but it will certainly stop the malware from spreading further. Once youve disconnected, proceed with your Apple malware removal process.
How To Remove Fake Pop
In most cases, pop-up scams do not infect users’ devices with malware. If you encountered a scam pop-up, simply closing it should be enough. In some cases scam, pop-ups may be hard to close in such cases – close your Internet browser and restart it.
In extremely rare cases, you might need to reset your Internet browser. For this, use our instructions explaining how to reset Internet browser settings.
Read Also: Lupin 500 For Tooth Infection
Your Mac Is Infectedand Not Protected
Sounds pretty shady, right? So why doesnt the Mac anti-malware program catch these guys? Typically, the makers of adware are hiding in plain sight, operating as actual corporations who claim to sell software on the level. They get away with it because their adware is often hidden in the fine print of a long installation agreement that most people skip over. Is it technically legal? Yes. You accepted the terms of the installment so they can spam you all they want. But is it right? So far, Apple hasnt stepped in to crack down on it. But if you ask us, the answer is an emphatic no.
In addition to adware, other potentially unwanted programs, such as so-called legitimate keyloggers, scammy cleaning apps, and faux antivirus programs that dont actually detect anything are skirting the Mac protections in place. So if a new form of malware makes its way onto your computer before Apple has a chance to learn about it and write code to protect against it, then youre out of luck.
So if you ask us, its time to start taking a closer look at your Mac. Is it acting the way your sturdy, reliable Mac has always behaved? Or is it exhibiting classic signs of guilt? If something seems a little off, you just might have a problem. Lets take a look at the telltale signs that your Mac is infected.
An Insidious Mac Malware Is Growing More Sophisticated
- Save Story
To revist this article, visit My Profile, then View saved stories.
- Save Story
To revist this article, visit My Profile, then View saved stories.
Mac malware known as UpdateAgent has been spreading for more than a year, and it is growing increasingly malevolent as its developers add new bells and whistles. The additions include the pushing of an aggressive second-stage adware payload that installs a persistent backdoor on infected Macs.
This story originally appeared on Ars Technica, a trusted source for technology news, tech policy analysis, reviews, and more. Ars is owned by WIRED’s parent company, Condé Nast.
The UpdateAgent malware family began circulating no later than November or December 2020 as a relatively basic information-stealer. It collected product names, version numbers, and other basic system information. Its methods of persistencethat is, the ability to run each time a Mac bootswere also fairly rudimentary.
Over time, Microsoft said on Wednesday, UpdateAgent has grown increasingly advanced. Besides the data sent to the attacker server, the app also sends heartbeats that let attackers know if the malware is still running. It also installs adware known as Adload.
Microsoft researchers wrote:
The following timeline illustrates the evolution.
Once installed, the malware collects the system info and sends it to the attackers control server and takes a host of other actions. The attack chain of the latest exploit looks like this:
Read Also: I Always Feel Like I Have A Bladder Infection
Detecting And Avoiding Spyware
Mac spyware exists. Spector was perhaps the first example of commercial spyware available for the Mac. Advertising-supported applications may also collect and disseminate your personal information without your knowledge. If you value your privacy, review the license agreement before installing or using any ad-supported application for information concerning how it protects your privacy. You may want to contact the application’s developer to determine if an ad-supported application employs spyware.
Applications are emerging to address the nascent market for detecting Mac spyware. These applications operate under the assumption that any application attempting to establish a network connection is potentially spyware. When an application attempts to establish a network connection, you are alerted. The alert identifies the application which requested a network connection, and gives you the option to permit or deny that application’s request to establish a network connection on a one-time or permanent basis.
Two such applications are:
Potentially Unwanted Programs Removal:
Remove PUP-related potentially unwanted applications from your “Applications” folder:
Click the Finder icon. In the Finder window, select Applications. In the applications folder, look for MPlayerX,NicePlayer, or other suspicious applications and drag them to the Trash. After removing the potentially unwanted application that cause online ads, scan your Mac for any remaining unwanted components.
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. Limited seven days free trial available. Combo Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk.com read more.
Don’t Miss: Kidney And Bladder Infection At The Same Time